The internet of things security anxieties are related to the protection of the data that is collected from all the devices interconnected over the Internet. Persons and companies are worried about all the sensitive information traveling through networks and stored in the cloud and how this data is guarded 24/7 from cyber-attacks.
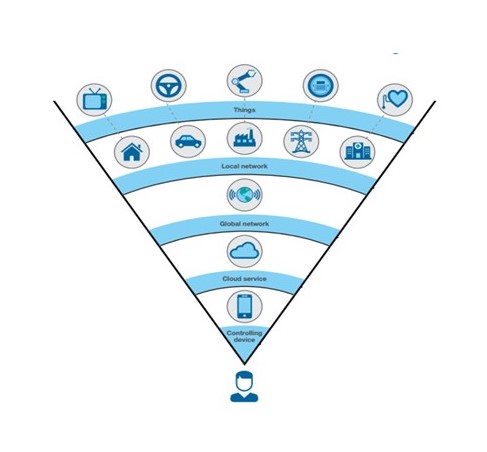
Persons and companies need to be certain about one thing, unauthorized parties must not be able to hack into IoT communications to steal and misuse data. In this case, identity management is the key to managing the risks of millions of devices being able to access too much information.
What is identity management? It is the identification of the device user role, analyzing how they are using their rights (what are the actions a device user is allowed to execute), and assess whether the actions executed are under the framework defined for the role. This includes types of device, products, and services associated to the device user and the role.
Companies must work to mitigate the effects of hacking; the key is to clearly define what are the fundamental identity rights and devices/applications security privileges to access them. This is critical because IoT is generating and passing information between devices and systems constantly.
IoT Security needs to identify the frame of reference of the data generated by the devices. According to the experts, this will be only possible by creating security solutions combining identity rights and devices/applications access privileges. Security professionals should build a framework where they can handle more complex aggregate identity information that is scalable
IoT Security needs to identify the frame of reference of the data generated by the devices. According to the experts, this will be only possible creating security solutions combining identity rights and devices/applications access privileges. Security professionals should build a framework where they can handle more complex aggregate identity information, and is scalable.
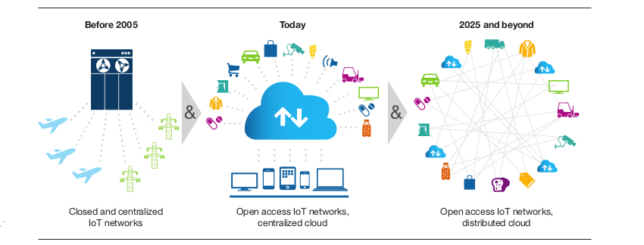
OASIS (a nonprofit consortium that drives the development, convergence and adoption of open standards for the global information society), is developing a privacy management reference model to help technology developers and service providers to translate laws, regulations and policies into effective measures they can take in the design phase. This is one of several new and emerging methodologies, frameworks and standards that can help to identify security and privacy risks, as well as help find ways of addressing them.
One reality though is that IoT companies are focus on revenue and profit and the primary goal is push product and service to the market in the short amount of time possible leaving security and privacy as a secondary goal.
Conclusion:

Most IoT users nowadays want assurances that the information they allow to flow into devices/applications will be used only in the way they have approved, and that it will be encrypted in order to avoid be accessed by any hacker or unauthorized device user.
This means that developers and suppliers of IoT products and services will increasingly be required to demonstrate that their offerings meet the privacy and security expectations of users.
Device users should pay attention to the security aspect of an IoT device/application and consciously evaluate potential security risks. We are responsible of our own security and privacy not the IoT vendors.

Pingback: Internet of Things – Vision of the Future of IoT in HR • The Internet of Things
Pingback: IoT Manufacturing – IIoT Evolution to Smart Manufacturing (Part 2 of 3) • The Internet of Things